CloudFormation Quick create: Creating an S3 Bucket and IAM User
CloudFormation's "Quick Create stack" feature enables point-and-click deploy of secure AWS architectures.
April 11, 2020 | aws cloudformation | by: Colin Dellow
Just want to create an S3 bucket and IAM user? Click here to use our precanned template.
AWS is infinitely configurable. That flexibility comes with a steep learning curve. Even when it's not difficult, doing things "the right way" can be tedious. That means people take shortcuts, like re-using security credentials or authoring overly-permissive security policies.
S3 buckets are a great example. They can act as the airlock between an organization and their service providers. Unfortunately, people often make their buckets world-readable/world-writable or share their all-powerful root user credentials rather than a more locked-down IAM user.
In theory, CloudFormation templates offer a solution. We could create a template that creates an S3 bucket, creates an IAM user who only has permission to read/write that bucket, and returns the user's access keys. Unfortunately, the standard AWS CloudFormation UI when creating a stack is... daunting. There are 4 screens of increasing length to navigate through:
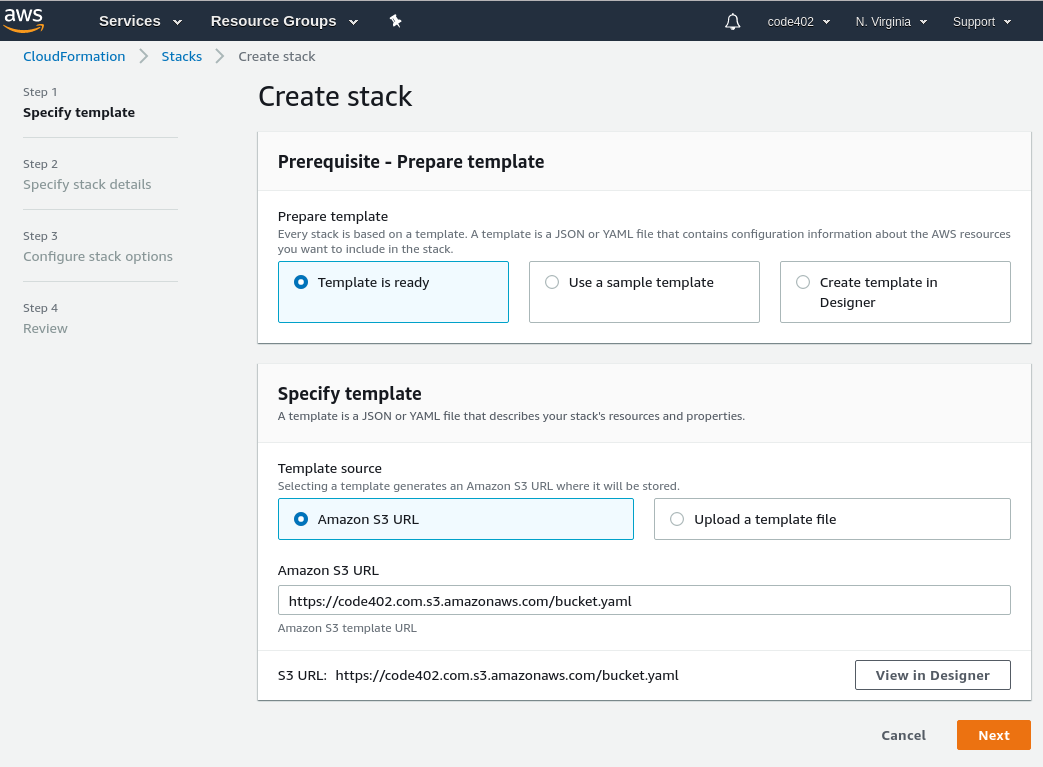
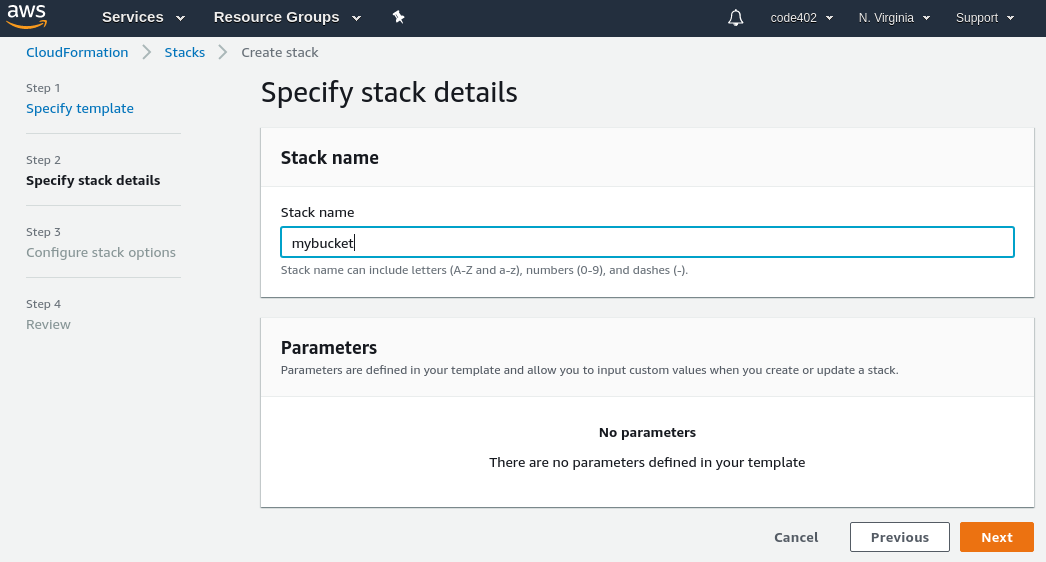
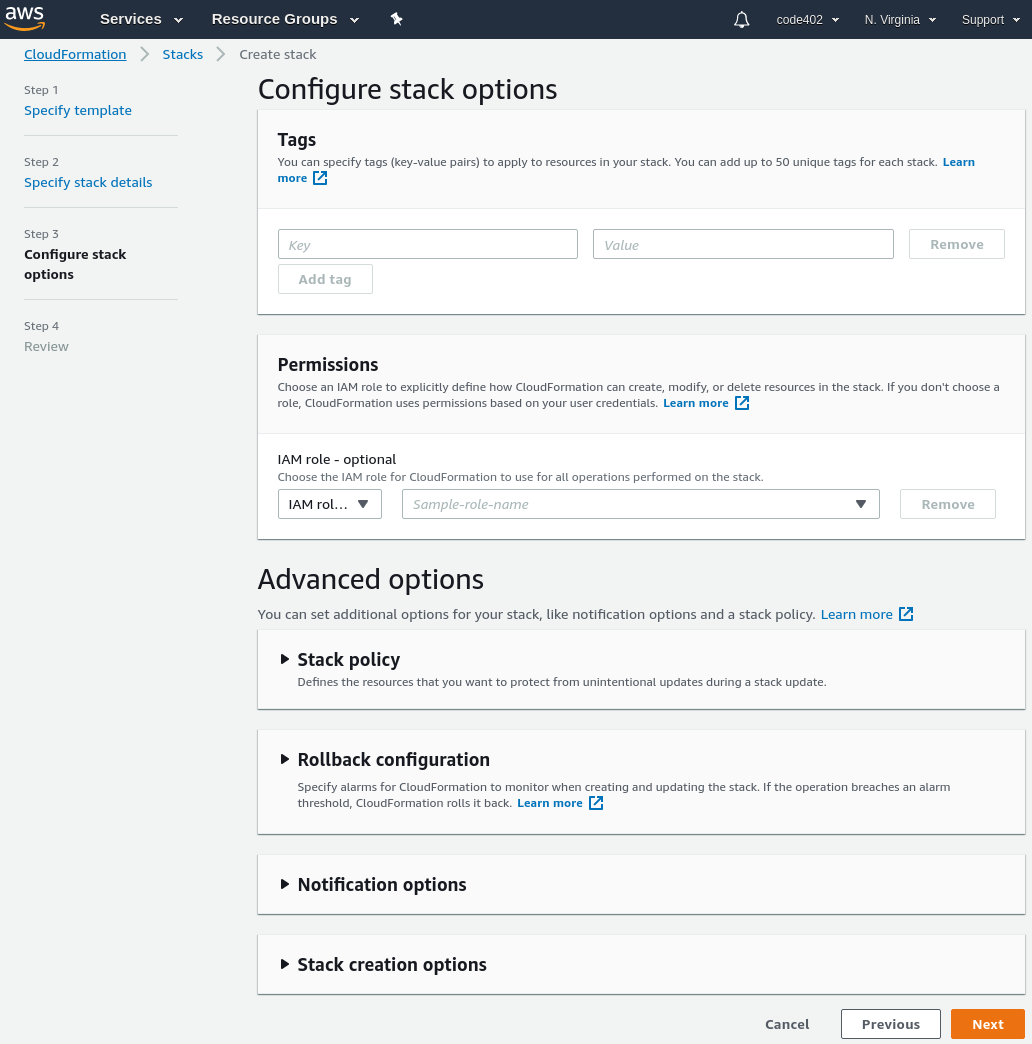
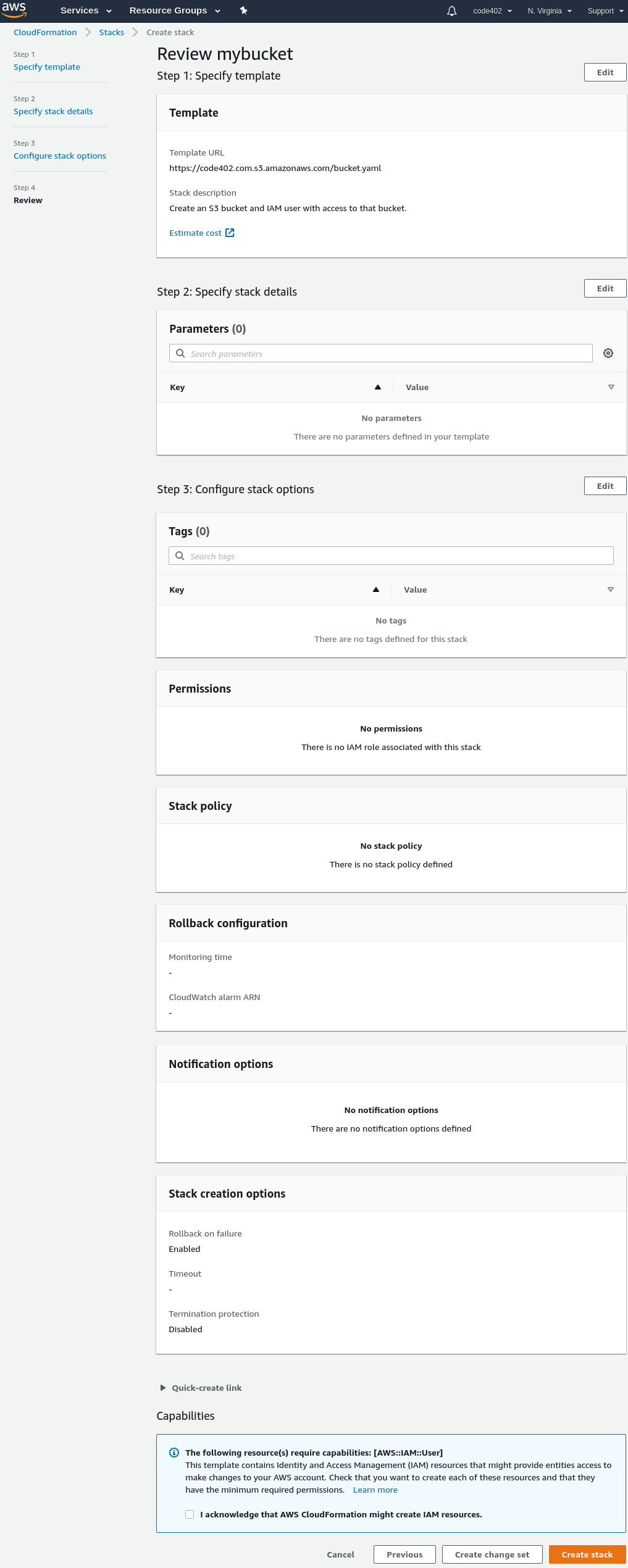
"Quick create" to the rescue!
The "quick create" feature from 2017 dramatically simplifies the process to a single screen:
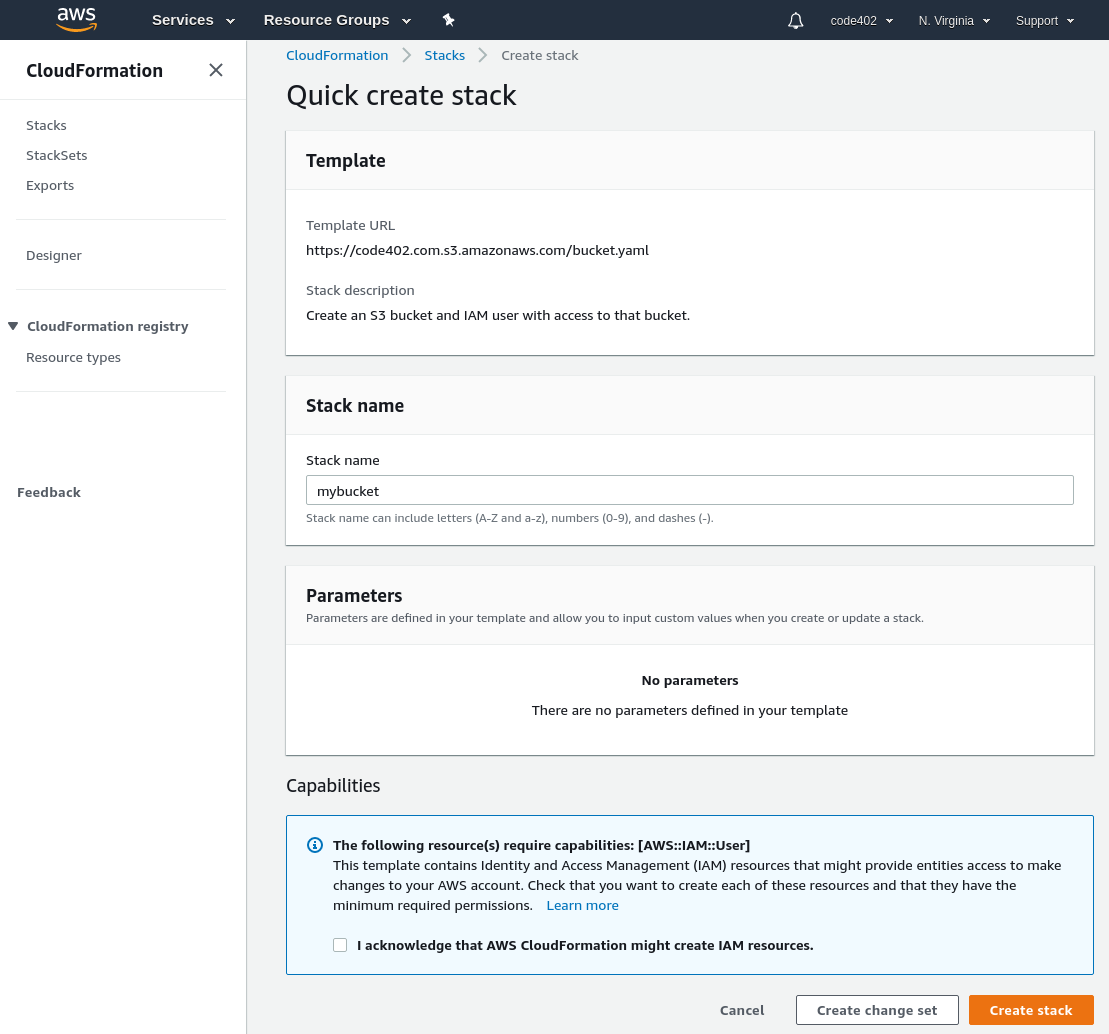
You can deploy your own bucket and IAM user here. Note that it publishes the IAM user's access key and secret key as an Output of the stack. This is, strictly speaking, a bad practice -- it means that anyone in the organization that has access to the stack can see the credentials, as can Amazon's technical support staff. Overall, it's a pragmatic security tradeoff that I believe still results in a better security posture. If you're not comfortable with that, you can issue the IAM user a new credential via the IAM UI.
For reference, the stack it uses is: